Enterprise Content Management (ECM): The Document Lifecycle

Enterprise Content Management (ECM) can be defined as the strategies, methods, and tools used to capture, manage, process, and deliver content and documents throughout an enterprise setting.
Because of the complexity surrounding enterprises and the vast amount of unstructured internal information going around within companies, content management in enterprise can be particularly challenging.
PDF Solutions: How the PDF is the old digital world made new again

When was the last time you opened a PDF document? Chances are, not too long ago at all!
In today’s digital world, the shift from hardcopies to digital media is as apparent as ever.
With books, magazines, journals, and all sorts of written and graphic information being digitized, the PDF has established itself as a leader in this industry-changing era.
Print Management – How to Prevent Printer Security Breaches
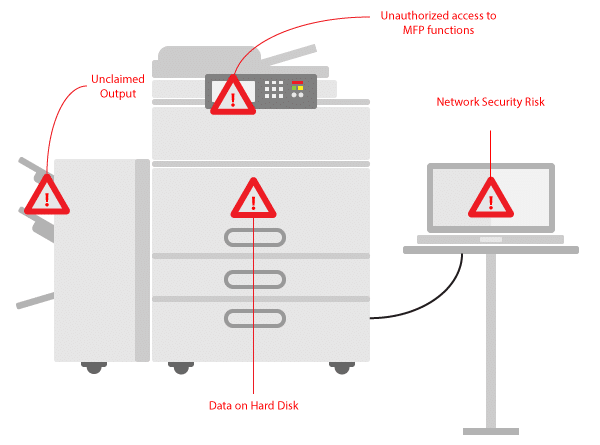
Over 60% of businesses have admitted to experiencing print-related data breaches, however enterprises still place a low priority on print security.
Multi-function printers (MFP) have evolved into sophisticated devices capable of running its own software and handling print, scan, email, and fax; it has become an integral device in streamlining workflows, and a device that organizations can no longer be complacent with. MFPs are referred to as the “weakest link” in IT infrastructure and can leave organizations exposed to potential data breaches.
Secure Print Release: 3 Ways to Securely Print Your Documents

Every enterprise strives to make existing business processes and workflows more efficient and ultimately to reduce costs.
In a busy organization, documents are often left at a printer or forgotten about. Depending on the department or industry, this can be a huge security risk.
Secure print release solves this by giving you control to print your print jobs when and where you want without having to worry about any security risks.
5 Reasons Why You Should Deploy Secure Pull Printing
It is no surprise that technology and software will always have holes that hackers want to exploit. With increasing security concerns surrounding hackers and data leakage, it’s no surprise organizations are beginning to beef up their IT security, with one of them being secure printing.
You can think of secure pull printing as a two-step process for your it printing environment. The first step being that a user sends a print job to a printer. The second part, is the authentication and release of the actual print document at the printer. Essentially, your print job will follow you wherever you go, allowing you to pick up a print job wherever and whenever you want.